This post is over a year old. If any of the information seems outdated or is inaccurate, please drop me an email and I'll be happy to update it.
Firejail is “an SUID program that reduces the risk of security breaches by restricting the running environment of untrusted applications using Linux namespaces and seccomp-bpf.”
In a nutshell, it’s a sandboxing utility that prevents applications from interacting with the filesystem. It works out of the box and ships with default configurations to run many common applications in a secure manner.
I’ll go through setting up Firefox for times when it’s handy to open a browser instance that’s sealed off from the rest of the system (e.g. when opening a suspicious link, banking online, and so forth).
Installing Firejail
The first step is to install firejail and X11 utilities. On Debian/Ubuntu this is as simple as using the available packages:
sudo apt install firejail xpra xserver-xephyr -yFirejail can integrate with PulseAudio on Linux for better compatibility, so it’s a good idea to activate this using the built-in configuration tool:
firecfg --fix-soundConfiguring Firejail Defaults
Google Chrome and a few other applications require privilege escalation in order to function correctly. Thankfully Firefox will not exhibit this behavior, so it’s best to enable Firejail’s sensible defaults where privilege escalation is concerned:
nano /etc/firejail/firejail.config
# change the config option below in the above file
force-nonewprivs yes Next, you’ll take ownership of firejail executable as the non-root user. Replace paramdeo with your own username:
chown root:paramdeo /usr/bin/firejail
sudo chmod u+s /usr/bin/firejailRunning Firefox In A Sandbox
To run Firefox in a sandboxed environment, we’ll simply use the following syntax to have Firejail start the application from the command line:
firejail --private firefox -no-remoteThe flags used in the firejail command have the following effect:
--private— restricts the folders visible to Firefox toDownloads, and uses a temporary profile that is nuked on exit-no-remote— allows sandboxed process to spawn independently of any existing open Firefox windows
The screenshot below shows what Firefox will look like when opened:
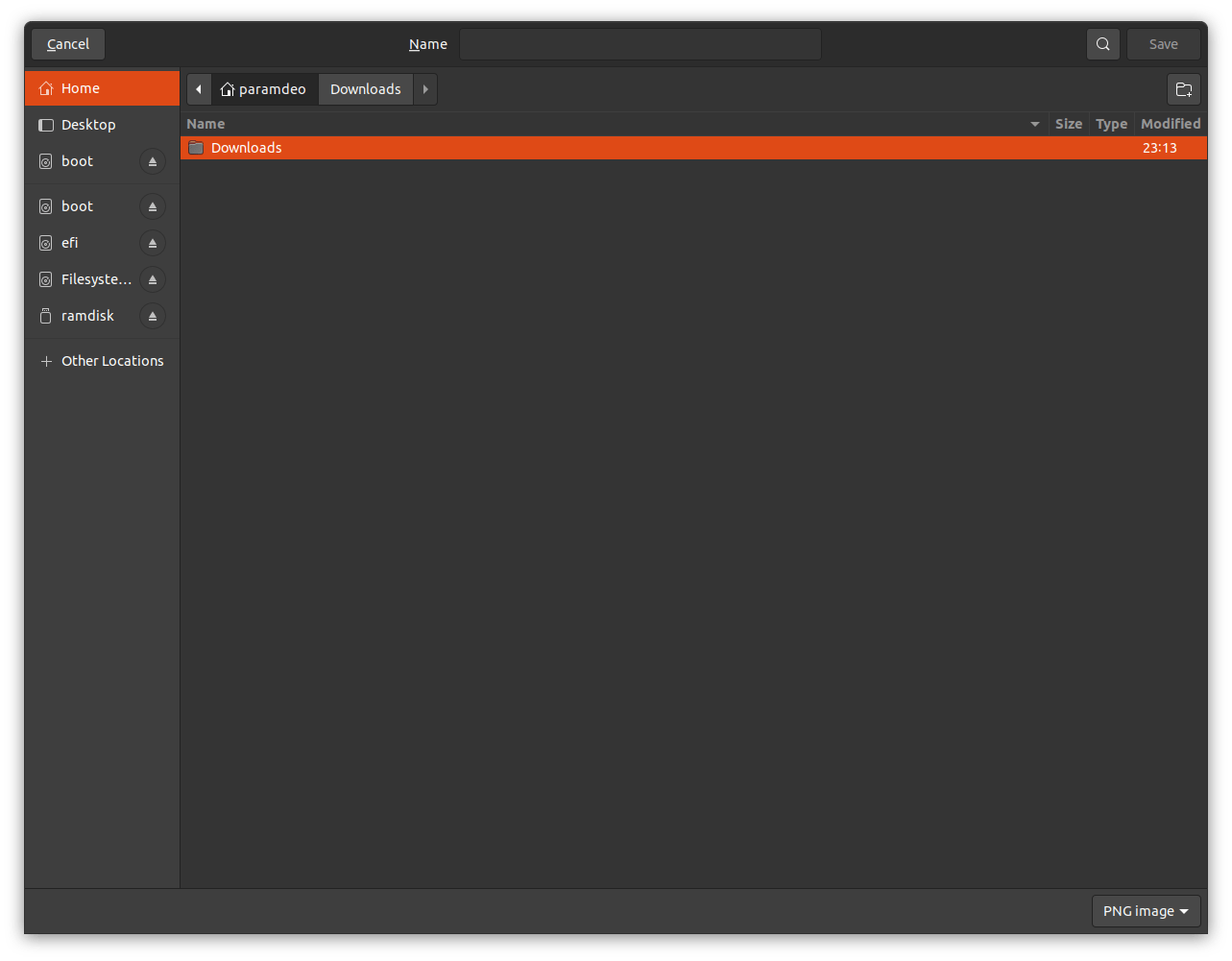
The screenshot below shows the locations available when attempting to save a file (and thereby browsing the user directory). Attempting to save anywhere other than the Downloads folder will result in a permission error.
An optional final step is to create a handy shell alias for ease of use. Add the following to your shell configuration file, replacing jailfox as an example with whatever you prefer. Since you’ll most likely use shell completion, choose something unique that you can easily Tab to suggest:
alias jailfox="firejail --private firefox -no-remote"And that’s pretty much it.
Links
- Firejail Project - firejail.wordpress.com